Surveillance and intelligence: understanding the benefits of Cyber Threat Intelligence

Yacine

What is Cyber Threat Intelligence?
Cyber Threat Intelligence (CTI) is an approach that involves collecting, analysing and disseminating information about threats, in order to anticipate and prevent computer attacks. CTI is playing an increasingly important role in a company’s security strategy. It enables us to understand who the attackers are, how they operate and, above all, to anticipate. To do this, CTI characterises threats based on their techniques, tactics and procedures (TTP).
Why integrate CTI for active surveillance and advanced threat detection?
At a time when cyber attacks are becoming increasingly targeted and complex, integrating CTI into a company’s cyber security strategy is no longer an option – it’s a necessity. CTI makes it possible to anticipate the behaviour of attackers based on concrete, actionable data. It enhances a company’s security by giving it a better understanding of its threat environment. Beyond anticipation, CTI also plays a crucial role in controlling the financial and operational consequences of attacks.
One of the applications of CTI is the continuous analysis of the external attack surface, i.e. all the points of entry accessible from the Internet. By cross-referencing CTI information with exposed assets, a company can identify vulnerabilities to an attacker before they are exploited. It can also detect mistakenly exposed services, such as administration interfaces or uncontrolled open ports. CTI also helps identify data or configuration leaks from open sources, which widen the attack surface. By monitoring this exposure, an organisation can prioritise remediation and adjust its defences in a targeted way.
Strengthen your security posture with attack surface intelligence
CTI enables companies to take a proactive stance. By understanding the techniques, tactics and procedures used by cyber attackers, security teams can anticipate attacks before they happen. This enables them to put in place appropriate defence mechanisms to completely prevent a vulnerability from being exploited. Beyond anticipation, CTI also plays a crucial role in controlling the financial and operational consequences of attacks.
Proactive detection, attack anticipation and response time reduction
Leveraging intelligence from CTI helps to detect suspicious activity earlier, limiting its potential impact. A Poneman Institute study shows that companies using CTI reduce their incident response time by 58%. By reducing incident response times, CTI also helps reduce operational costs and economic losses associated with cyber attacks. In addition to the economic impact that CTI can have on a company, it also makes it possible to better organise internal efforts and mobilise the right resources.
Intelligent surveillance and intelligence-led offensive posture
CTI helps to identify the threats that are really relevant to the organisation, thus avoiding security efforts being spread too thinly over unnecessary or out-of-context alerts. It also enables actions to be prioritised more effectively and human and technical resources to be focused on what is deemed relevant. Finally, effective CTI contributes to the continuous improvement of defences by capitalising on the knowledge acquired.
Based on constant monitoring and constantly updated data, CTI enhances the existing security strategy. It feeds the defence processes with indicators of compromise, emerging threats and attacker profiles. It’s a continuous learning loop that forms part of the company’s security culture.
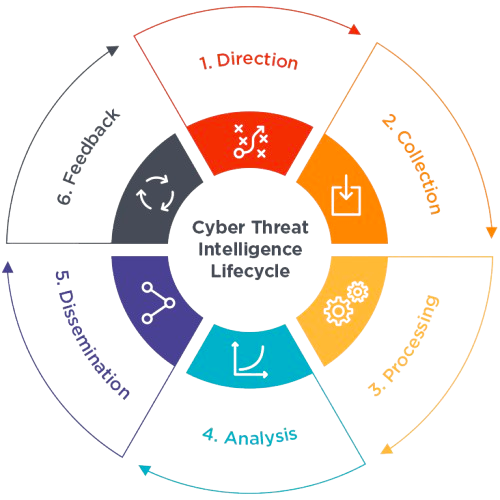
CTI methodology: from collection to transformation into usable intelligence.
The integration of CTI is based on a rigorous methodology that follows a cycle of information processing in several key stages:
Collecting information:
This stage consists of recovering as much data as possible relating to suspicious behaviour, current or past attack campaigns, or recently discovered vulnerabilities. This information can come from public (OSINT), technical (logs, alerts, etc.), commercial or even human sources.
Example: Identifying a domain used in an ongoing phishing campaign
Analyze
Not all the information collected is necessarily relevant and useful. The role of a CTI analyst is to extract what is important and interpret it. The aim is to understand the context by asking 3 questions:
- Who is behind the attack?
- What are its objectives?
- What tools is the attacker using?
Turning information into intelligence:
Once the information has been analysed and contextualised, it becomes intelligence. This intelligence can be exploited by SOC teams, whose aim is to monitor, detect and react to incidents in real time to protect businesses.
Protecting yourself before the attack :
The whole point of the CTI lies in its ability to act upstream by implementing concrete actions such as..:
- Fixing a flaw
- Raising team awareness
- Blocking an indicator

Key intelligence sources: effectively monitoring your attack surface
To provide relevant and usable information, CTI relies on multiple sources of information, each with its own specific features and advantages:
Open Source Intelligence (OSINT)
These sources include social networks, specialist blogs, public forums, RSS feeds, as well as collaborative platforms such as VirusTotal, MISP or MITRE ATT&CK. Popular tools used in this category include Maltego, Shodan, SpiderFoot and Recon-ng. OSINT is a valuable information base for spotting and identifying new malicious campaigns or detecting the first traces of a threat. OSINT is accessible to everyone, making it indispensable, although it does require rigorous sorting and analysis to eliminate false positives.
Sources techniques
They include event logs, firewall data, IDS/IPS data and malware analysis. Automated tools such as SIEMs (Splunk, QRadar, ELK), as well as complementary solutions such as Wireshark or Zeek (Bro), play a crucial role in the effective exploitation of this technical data.
This data, although raw and often in quantity, is essential for identifying the weak signs of a compromise, building technical indicators (malicious IP, suspect file name, malware hash, etc.) and refining detection in real time. They enable close correlation between current and past events.
Commercial sources
These are information feeds provided by suppliers specialising in threat intelligence. These sources charge a fee, but offer highly accurate and reliable data, enhanced by expert analysis. Services such as Recorded Future, CrowdStrike, FireEye and Digital Shadows are benchmarks in this field.
human sources (HUMINT)
Human intelligence, or HUMINT, is based on exchanges between cybersecurity professionals: SOC analysts, CERT teams, CISOs, researchers, etc.
Human intelligence also includes feedback, internal investigations, and discussions within certain business sectors or communities (e.g. ISAC). HUMINT is often the missing piece in contextualising a threat and gaining a better understanding of its intentions.
Dark Web and Deep Web
Exploring these less accessible digital spaces can reveal crucial information about planned attacks, exploited vulnerabilities or compromised sensitive data before it even becomes public, and specialist tools such as Tor, DarkOwl and Flashpoint make such explorations easy.
Example of a Cyber Threat Intelligence use case: Monitoring a proactive Underground team group.
Context
Over the last few months, we have seen the rise of a little-known but active ransomware group. Underground Team. This group, which uses well-established double extortion techniques, mainly targets international companies in a variety of sectors (health, industry, technology, etc.).
Their modus operandi is clear: they penetrate a company’s networks via phishing emails containing malicious attachments. Once these have been downloaded, they run on the victim’s computer to extract several hundred gigabytes of sensitive data. This data is encrypted with the ransomware. If the ransom is not paid, the stolen data is published on the Dark Web, as was the case for Ethypharm, Bulldog Bag Ltd and other companies.
Triggering the alert
It all started with a post spotted on an .onion site (the extension for sites hosted on the dark web), run by the Underground group.
The group provides a chat platform so that victims can talk to them through a ticketing system.
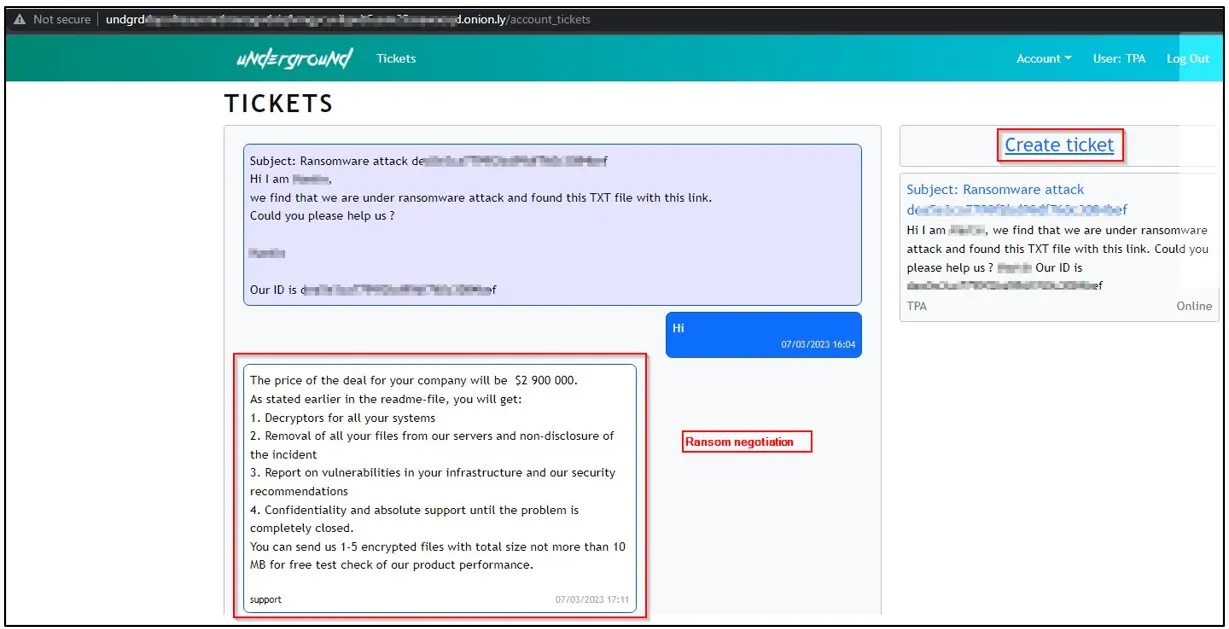
source : https://thecyberexpress.com/newbie-group-underground-team-ransomware-group/
Confidential data belonging to an organization had just been posted online. CTI’s monitoring of underground forums and Telegram has identified this group’s activity. This gives them an advantage in preventing future attacks.
Example of a message received by victims:
source : https://www.ransomlook.io/search
Actions taken by the CTI team
To counter these attacks, several CTI actions have been put in place:
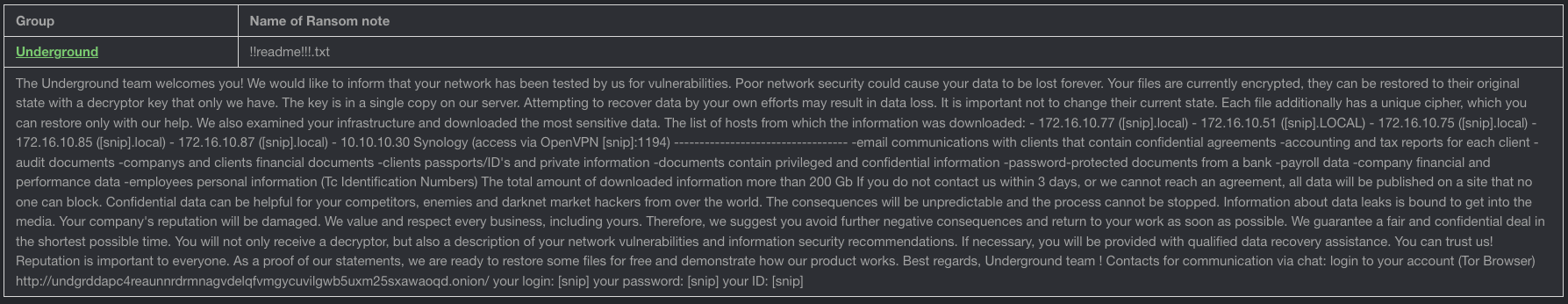
- Analysis of indices of compromise (IOCs):here an IP address of a C2 server was recovered, hashed suspicious files and identified their typical ransom note, named !!readme!!!.txt
- Mapping the group’s techniques, tactics and procedures using the MITRE ATT&CK database:
- T1566.001: Phishing with attachment
- T1021.001: Lateral via RDP (Remote Desktop Protocol)
- T1041: Exfiltration of data via an external channel
- Real-time monitoring of new victims posted on their ‘Hall of shame’ via their .onion site
- Working with SOC teams to enhance SIEM/EDR rules
Results
Thanks to this active monitoring, a targeted phishing attempt was detected and blocked. The email contained a booby-trapped attachment which, if opened, could have been used to deploy the Underground ransomware. Post-incident analysis revealed that it was probably a known loader (such as GuLoader or Qakbot). This rapid detection enabled the attack chain to be blocked before it was compromised. At the same time, security measures were put in place to secure RDP access.
This clearly shows the extent to which cyber threat intelligence is essential for a company. CTI is not just about collecting information, it’s about anticipating threats, understanding attackers’ modus operandi and acting quickly to block intrusion attempts.
Conclusion: Cyber Threat Intelligence, an essential tool for modern cyber security
As threats intensify and become more complex, integrating Cyber Threat Intelligence into the heart of security strategy is no longer an option, but a necessity. Thanks to its various sources, CTI provides the intelligence needed to prevent, anticipate and respond effectively to cyber attacks. It is by relying on this proactive intelligence that businesses will be able to navigate more serenely in an increasingly demanding digital environment.
This clearly shows the extent to which cyber threat intelligence is essential for a company. CTI is not just about collecting information, it is about anticipating threats, understanding attackers’ modus operandi and acting quickly to block intrusion attempts.
Discover our other articles
Cyberattack: how do hackers get into your systems and exploit data?
The purpose of this first article is to present data leaks comprehensively, covering their...
Google Dorks
Google dorks are Google queries that allow you to find information more accurately by...
Surveillance and intelligence: understanding the benefits of Cyber Threat Intelligence
Surveillance and intelligence: understanding the benefits of Cyber Threat Intelligence Yacine 16 May 2025...