
Protecting against external cyber threats
External cybersecurity threats are constantly on the increase, fueled by a growing number of malicious actors and automated “attack tools”. Attack vectors are multiple.
Data leaks can have far-reaching repercussions for companies and organizations, causing major losses on several levels.
Stolen data become tools and a financial source for cybercriminals: they can fuel phishing attacks, be resold on the Dark Web or exploit strategic advantages.
The incident can cause business interruption, slowing down operations and resulting in lost sales.
Data leaks can also have a reputational impact, leading to a loss of trust among the affected organization’s customers and partners.
Protect your data
AlgoLightHouse covers password leaks within data breaches, content monitoring of unstructured data sites and Telegram groups of attackers (info-stealers).
Phishing primarily involves the theft of credentials or the installation of malicious software (malware) with the aim of compromising internal information systems or stealing sensitive (financial, strategic) data.
The purposes can be of several kinds : data resale, ransom demands, president fraud…
"Phishing remains the most frequent attack vector, with 74% of companies declaring phishing as the main entry vector for attacks suffered."
Source : 9th edition of the CESIN annual barometer
Anticipate phishing !
By monitoring domain names, AlgoLightHouse can keep an eye on Typosquatting and anticipate malicious campaigns.
Vulnerabilities, whether Zero-Day or One-Day vulnerabilities, obsolete services or misconfigurations, widen the company’s exposure perimeter.
Malicious individuals take advantage of these vulnerabilities to infiltrate systems. For example, with automated recognition and exploitation tools, attackers can perform enumeration activities facilitating future compromise of the information system.
By integrating continuous scanning, mapping and active monitoring solutions, AlgoLightHouse reduces the risk of intrusion via these potential entry points.
Shadow IT represents a major challenge to detect and manage in order to secure the entire information system. By evading the recommendations of IT teams, Shadow IT exposes companies to risks ranging from minor to critical. The use of unauthorized tools creates security loopholes and increases the attack surface. Indeed, every new application or service used without validation adds a potential entry point for cyberattacks.
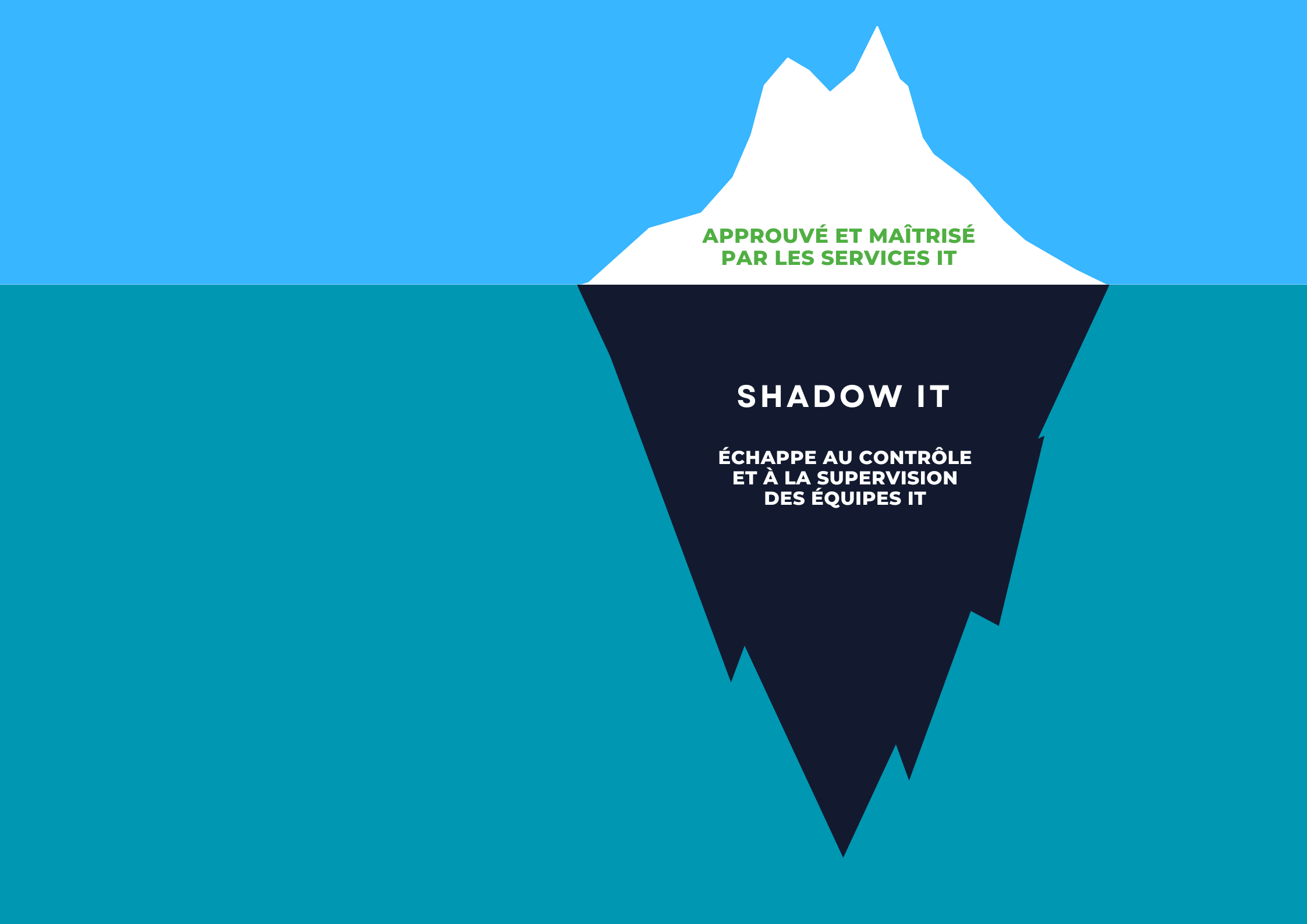
Detect the invisible
Gain visibility of potential vulnerabilities and data leaks linked to applications or services or services not integrated into your IT scope.
For organizations, the Dark Web and social networks represent a growing threat, both to data security and to the integrity of their image.
The Dark Web and social networks are a breeding ground for the exchange of sensitive data, including sensitive data leaks. Cybercriminals use the Dark Web to sell or exchange organizations’ sensitive information, such as login credentials, financial data… This data can then be used to carry out targeted attacks, such as fraud or extortion.
Coupled with OSINT and expert analysis, our service includes monitoring of social networks and the Dark Web.
To find out more about cyber threats, we recommend reading the panorama of the cyber threat published each year by ANSSI. https://cyber.gouv.fr/actualites/lanssi-publie-le-panorama-de-la-cybermenace-2023


